In the field of cybersecurity, social engineering is referred to as the act of deceiving or hacking people into making wrong moves or poor decisions. The primary objective is to take advantage of potential victims by psychologically manipulating them with their emotional responses and natural tendencies. The attacker uses their victim’s curiosity, fear, selfishness, and desire to help others, in tricking them into doing wrongful acts.
A social engineering fraudster can execute the attack in steps similar to these:
- Getting ready for the attack. The preparation includes carefully identifying the potential victim, gathering the necessary information to seem less suspicious during the attack, and choosing an attack method.
- Tricking the victim. The perpetrator will then engage the target in conversation or send messages that usually include deceiving stories to gain the victim’s trust.
- Acquiring the victim’s personal and confidential information. After careful manipulation to gain the victim’s trust, the perpetrator can obtain sensitive information and data.
- Ending the interaction. The perpetrator will cautiously and naturally close the interaction with the victim—leaving no traces of malicious intent.
Most common forms of social engineering attacks
Now that we know what social engineering is, let’s look at the attack techniques or how cybercriminals usually carry out their malicious intent.
Phishing
Phishing is the most prevalent form of fraudulent activity and social engineering attack implemented through malicious emails, text messages, or phone calls. The fraudster tricks its victims by pretending to be a legitimate email provider or representative of a company or institution, like banks, stores, and known corporations.
Here’s an example of what it may look like:
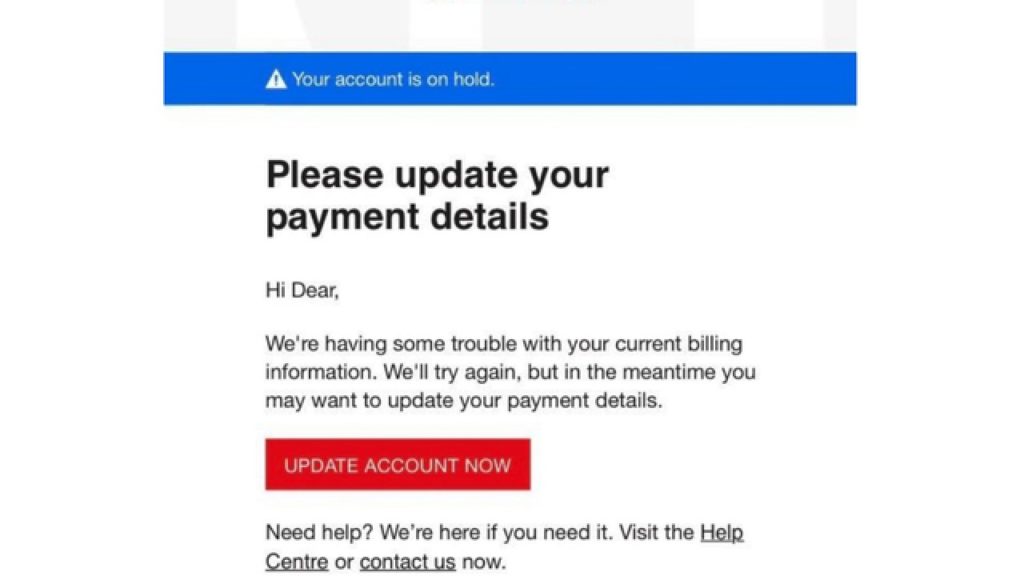
Phishing messages usually call for immediate action about a victim’s account. Fraudsters often send messages saying that an update is needed, that there’s suspicious activity, or a need to confirm their identity, and then require personal information from the victims.
In other cases, fraudsters will ask to click a malicious link. This is also present in social media platforms, where fraudsters lure people into bitcoin phishing scams.
Here’s an example of a phishing scam done via Twitter:
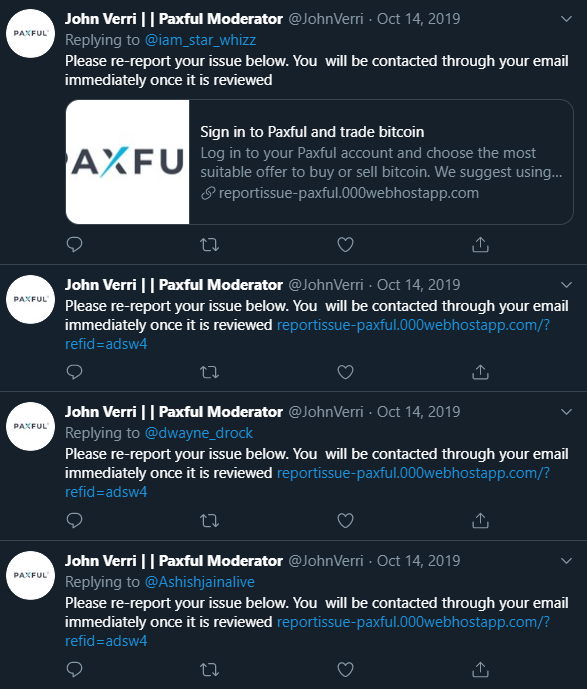
Here, the fraudster pretends to be someone from Paxful and asks potential victims to click a link where issues about accounts should be reported. When clicked, this malicious link will gather all the essential and confidential information—in this case, bitcoin wallets addresses—of their victims.
Spear Phishing
This is a type of phishing scam, but more targeted. In spear phishing, fraudsters carefully choose their specific target individuals or companies. To make the attack harder to detect, they’ll tailor the messages based on their victims’ emails or conversations.
It usually happens like this: a perpetrator pretends to be someone the victim knows and asks for confidential information, such as personal login details to access a company’s sensitive files.
The email and all other messages may look legitimate, but the truth is they’re all infected by malware. Often, there’s a link redirecting the victim to the malicious page where login credentials and other details will be compromised.
Once the link has been clicked, the fraudster will be able to access and obtain the victim’s credentials and the company’s important data.
Baiting
This social engineering method uses baits to lure potential victims to enticing items or products that are infected by malware. Fraudsters usually do this through websites or clickable links that offer something for free—like a movie, book, or music copy, and other digital files.
The attacker can either ask the victim to create an account or simply click and download the malicious file immediately, which automatically infects the victim’s computer with malware.
Baiting can also happen in physical form, where fraudsters leave a malicious flash drive or hard drive in a public area, waiting for curious people to plug it into their computer and check what’s inside. Connecting it with a device infects the device with malware.
Scareware
Have you ever encountered a pop-up message on a website that says, “Your computer is infected! Click here to remove the malware” or “Warning! 74 infections found?” If you haven’t encountered any messages like that, lucky you! Here’s an example of how it usually looks:
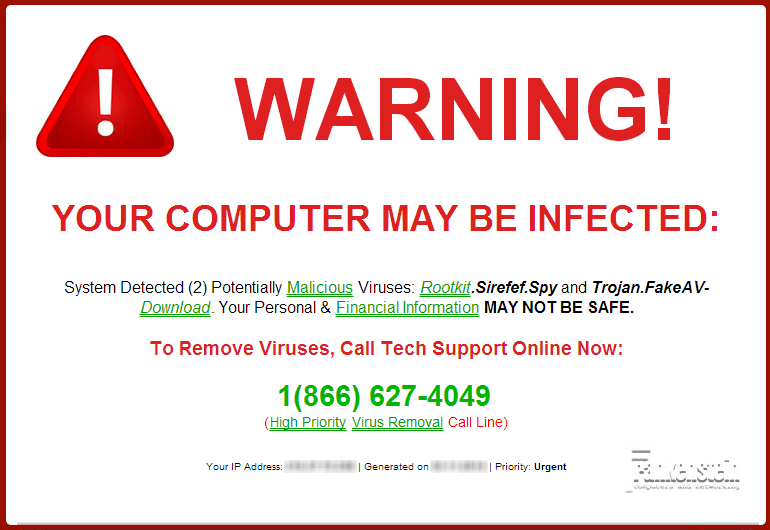
We hope you didn’t click on these seemingly legit pop-ups because these can harm your device severely.
This social engineering attack uses scare tactics to spread malware designed to frighten or shock its potential victims. It may ask you to click on an infected link or download malicious software. Doing either of these can compromise your computer.
Aside from deceitful pop-ups and banners, scareware can also be distributed through emails—usually about fake warnings and offers.
Pretexting
Here, the perpetrator pretends to be someone who’s allowed to know certain important information—it can be a bank or company representatives, police, or even co-workers, to name a few.
In this attack, perpetrators usually ask questions in gathering essential data. Like the social engineering schemes we’ve previously mentioned, once the perpetrator gains the potential victim’s trust, sensitive information like phone records, residential addresses, social security numbers, and the like can be obtained instantly.
Five ways to protect yourself from social engineering schemes
Now that we’re done defining the attack techniques and how each happens by providing some social engineering examples, let’s take a look at some tips and tricks on how you can get away from them and keep your bitcoin safe.
1. Be vigilant and cautious of email links and attachments.
Always be careful when opening emails, especially if you see suspicious subject lines or messages. Don’t just open an attachment or link. Check if the email, hard drive, or link source is credible and legitimate before clicking on it.
Remember, pop-up and banner ads, and unknown websites are also counted in the list. So, always be on the lookout and protect your bitcoin wallet and Paxful account, and other confidential information from cybersecurity and social engineering attacks.
2. Install reliable antivirus software.
Install secure and trustworthy antivirus software on your devices for an added layer of security. It’s also crucial to keep your computer and other personal devices’ operating systems and antivirus solutions up to date.
3. Use robust security solutions for your accounts.
Use strong combinations for account passwords. It’s also best if you can keep your passwords to yourself—remember, it’s meant to be kept confidential unlike usernames that can be shared with anyone. If you’re using system-generated passwords, which may be hard to remember, password storage software can be your best friend.
Stronger security options for your accounts include enabling two-factor authentication (2FA). If you haven’t enabled this on your Paxful account yet, do yourself a favor and head on to your account security settings!
4. Watch out for tempting offers.
Think twice or more before you click on enticing offers. Doing so can effectively keep you away from dangerous traps of social engineering schemes. If the offer seems too good to be true, there’s a high chance that it probably is. While that statement isn’t always true, it’s essential to be wary of such offers and try searching for them on the Internet before proceeding.
5. Educate yourself and read news about social engineering attacks.
You may ask, “What is the primary countermeasure to social engineering?” This is the answer to that question—do your research and share what you’ve learned about social engineering attacks with your friends, family, and colleagues. These conventional techniques are sometimes tough to detect, so teaching others about these schemes could be very helpful.
Secure your personal information and bitcoin wallet now!
It’s crucial to be always on the lookout for potential frauds and schemes in cyberspace. Fraudsters are always looking for ways to compromise every potential victim’s confidential information. This includes bitcoin accounts and wallets, as the crypto space is among the top targets of cybercriminals.
Keeping yourself updated about the latest malicious activities and attacks online will save you from dire consequences. Try exploring crypto news sites or your favorite antivirus software’s blog site—in case you have any.
Security solutions providers, such as Malwarebytes, Bitdefender, and others share extremely useful information about cybersecurity trends, malware protection and defense, and more. If you want to broaden your malware-dodging knowledge and skills further, you can also find firms online that provide threat management training.